For instance, between 2017 and 2020 the number of records exposed due to data leaks grew from 197 million up to 37 billion, though the total number of data leaks decreased. As IBM informs, only in the USA, between 2018 and 2020, the average cost of data leak for the companies that fell victim to cyberattacks grew from $ 7.91M to $ 8.64M.
A number of methods used by cyber criminals are based on a human’s mistake, when even the smartest employees’ unconscious clicks can lead to malicious links. While other cyberattack methods take advantage of your data security gaps to get access to your confidential data.
Here are 7 most common cyberattacks your organization can face in 2021 and ways to prevent the data leaking they can cause.
1.Malicious software attacks
Malware means numerous types of software aimed at infiltrating, spying on or creating a backdoor in an organization’s data system, including trojans, worms, ransomware, spyware and adware. According to experts’ reports, since the beginning of 2020 malware usage has grown up to 800%.
Malware can cause serious data leakage and disrupt business operations. For example, Microsoft fell victim to ransomware when WannaCry made use of its operation weak points and plenty of banks, medical service providers and other companies all over the world got one and the same message on their displays:
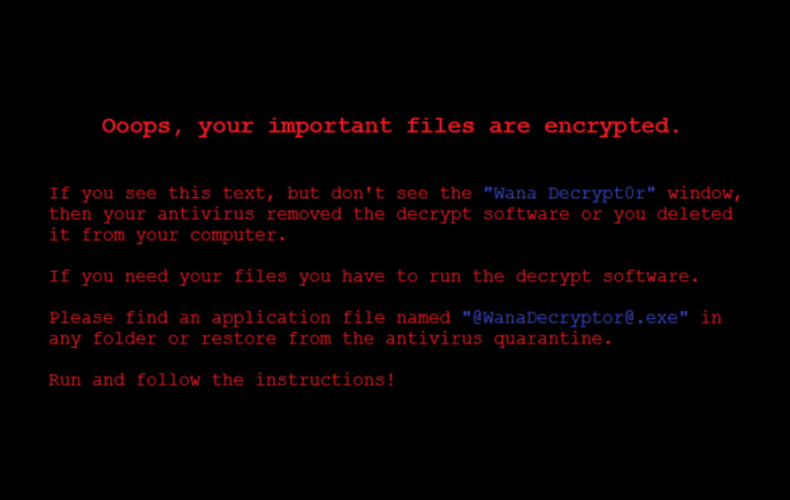
To restore access to their computers and also to all the unbacked-up files, companies had to pay redemption to WannaCry creators in Bitcoin.
Malware is usually downloaded unintentionally by clicking a malicious link when a user is made to think to be downloading something legal though it is not.
How to defend against malware attacks
Reduce the chance ofbeing infected by malicious software by teaching your employees how to detect suspicious links and pop up windows.
Use extra means of protection against malware, such as antivirus software and operating system renewal to patch known security gaps. For instance, Equifax data leak could have been prevented should a proper be installed timely.
2.Phishing attacks
Phishing attacks are aimed at stealing users’ information or making them download malicious software by sending emails and text messages. It is a scam though looks like a real request.
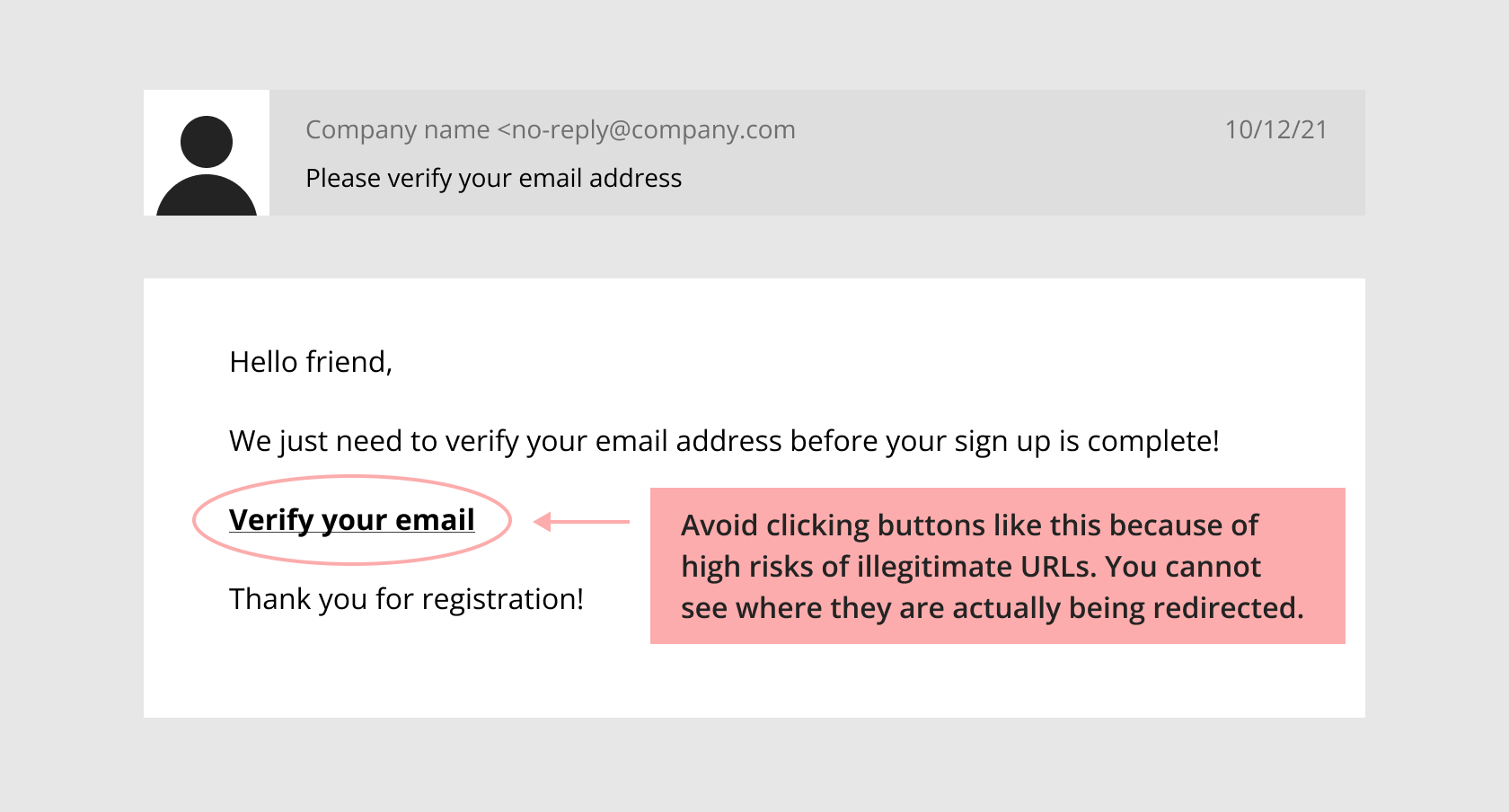
Verizon reports that phishing attacks are the most widely-spread reason for data leakage all over the world in 2021 and caused most prominent cases of cybercrime last decade. By breaching the AP News account the intruder falsely twitted that the White House fell victim to a targeted phishing attack (spear-phishing). So did the bad actors who breached the election campaign chairman’s confidential emails to Hillary Clinton before the 2016 election.
How to protect against phishing attacks
The best way to defend your company from phishing attacks is to educate your employees in identifying suspicious emails and text messages. CSO has made a list of sources that can assist you in teaching your teams how to detect phishing attacks.
3. DDoS attacks
DDoS (Distributed denial of service) attacks violate the traffic of an application, website, service or a server by suppressing it with a flow of a compromised computer net (botnet ) trafic, that prevents real users from gaining access to it. The hardest DDoS attack in history took place in 2018 when GitHub received 1,35 terabits of traffic per second and was offline for about 20 minutes as a result.
According to Kaspersky security company, DDoS attacks are a common thing and their number increased by 50% for only one year, the most significant surge occurring at the beginning of pandemic 2020.
How to protect yourself from Distributed denial of service attacks
DDoS attacks are tricky to identify as they are hardly differentiated from legitimate traffic. Some ways of protection include blocking of all traffic for a while, traffic rate-limitation to a website, using a web application firewall to detect suspicious traffic patterns, or distributing traffic across a network of servers to cut the attack’s effect.
4. Man-in-the-middle attacks
Man-in-the-middle (MtiM) attacks are made by bad actors who spy on you or intercept messages between you and your users or employees for stealing your personal or corporate information or for redirecting it to another place of destination or in espionage situations.
MitM attacks is a relatively rare cyber attack type as most of its goals can be achieved with the help of malicious software. Though, being hard to reveal, they may be of great danger for organizations especially since more employees are working remotely after 2020.
For example, remote employees often work in cafés or coffee shops where fake WiFi networks can be easily deployed. Connecting to these networks and using them, unwillingly, people fall victim to criminals’ espionage.
How to defend yourself from MitM attacks
The best way to protect yourself from MitM attacks is end-to-end encryption protocols such as Transport Layer Security (TLS). In addition to that, if your employees use VPN for corporate network access, any information shared during their session is guaranteed to remain private, no matter whether the network belongs to a malefactor or their coffee shop’s WiFi lacks security.
5. Credential stuffing attacks
Filling in credentials is a brute-force cyberattack method when intruders make use of once stolen usernames and passwords from one data leak to get access to another organization’s user account.
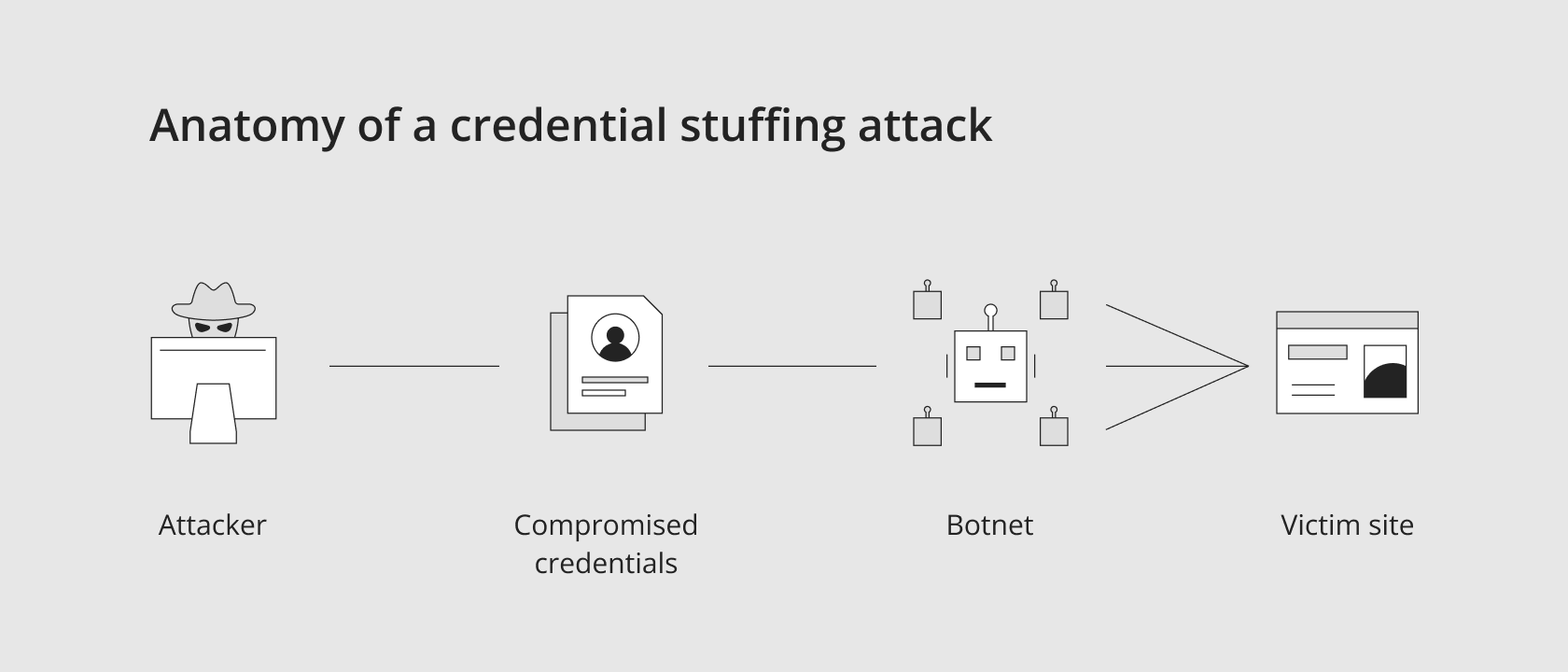
According to statistics, 65% of all people use one and the same password for several accounts, so credential stuffing attacks are very likely to occur. That is why filling in credentials is one of the most common reasons for data leakage in the world.
How to protect yourself from credential stuffing attacks
The best ways of preventing credential stuffing attacks are passwordless authentication and multi-factor authentication (MFA). Passwordless authentication prevents malefactors from using stolen credentials by eliminating them completely while MFA demands identity verification in one or more ways in addition to the stolen credentials that the intruders use to log in.
6. Password spraying attacks
Another type of brute-force attack is password spraying when intruders try to guess a user’s password from a list of mostly spread passwords such as “QWERTY”, “123456” or “password.”
Password spraying is as common as credential stuffing. So, according to Verizon’s 2020 Data Breach Report more than 80% of all hacking-related data leaks included brute-force methods like password spraying.
How to defend yourself against password spraying attacks
Password spraying attacks have much to do with credential stuffing attacks here, so using passwordless authentication or MFA, can prevent this type of cyber attack. Besides, following the NIST Password Guidelines can also be of great use, as they are considered the top password standards globally.
7. Mobile device attacks
Many organizations tend to elevate the mobility of their employees and, one the one hand, it improves operational efficiency and productivity. But on the other hand, cybercriminals, being aware of this fact, are focusing on mobile devices more and more often from year to year with various attacks mentioned above, which makes organizations more vulnerable to a data breach through more handheld devices than ever before.
So was Pegasus' attack on Apple’s iOS software. Phishing text messages asked iPhone holders receiving a text message to follow a link inside. Clicking the link started the installation of spyware capable of monitoring people through their camera and microphone. Should iPhone users be infected had their login credentials be stolen from Gmail, WhatsApp, and other susceptible communication applications.
How to defend against mobile device attacks
Both an excellent enterprise mobility management (EMM) program and mobile device management (MDM) tools will be of great help in protecting any company data that your employees may have on their personal or work devices. Unauthorized access to work applications containing sensitive information can also be prevented via multi-factor authentication and other identity and access tools.
Conclusion
Use strict authentication protocols. They will help to minimize, eliminate or totally prevent damage from cyberattacks from the above-mentioned list.
Do not forget about other protection tools. Start with sophisticated password policy and sound employee education. Multi-factor authentication or passwordless authentication together with brute force protection will add a new dimension of safety to your system.
The article has been based on the cybersecurity report 'The 7 Most Common Types of Cybersecurity Attacks in 2021'.



