A year and a half ago, the idea of remote work in the future, where we freely perform our work and cooperate with colleagues from anywhere, seemed engaging but an unlikely concept. And at one point, this future became the present.
The employees had to put up with a drastic change in their lifestyle. While the transition to remote work was a significant challenge for most organizations, it was also an opportunity to explore and accelerate the realization of plans, which were in the early stages of progress before the pandemic. It also allowed employees to experience a new way of working - remotely. For many people, the remote format provided an improved work-life balance and more time with their families.
As organizations and their employees begin, tentatively, to move to the post-covid stage of their lives, it remains unclear to what extent the changes and amendments of last year will remain in force.
For most, a complete return to office life from 9 to 5 seems extremely unlikely. But it is equally unlikely that the country's office buildings will stand silent and empty for several months in a row.
It is essential to consider how we would secure remote work in the future. What processes, policies, and tools are necessary to protect personnel, devices, and – most importantly-data.
How will the work be different in the future?
Work in the future will be different in how employees will access data and collaborate in the post-pandemic world.
What does this mean for security tools and policies?
Companies must have the same security policies wherever anyone works; two years ago, you could have gotten away with it. But now, any company must take care of data security in any format of its employees ' work.
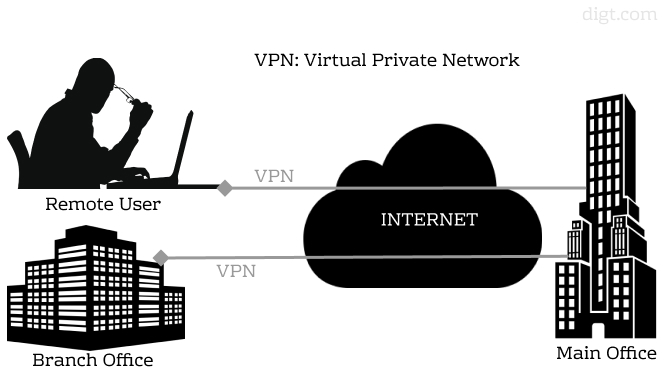
Many companies had already taken some steps before Covid so that their organizations could work remotely to a certain extent. A classic example was VPN gateways, usually used for a small part of users, but which have now expanded and become the basis of the entire organization, where everyone works remotely.
Cloud services that bring users and applications together are especially relevant for remote work now. Cloud service gives its users the best experience and is at the center of the processes.
It means that these connections do not have to pass through a central security stack at headquarters, as in the classic hub and spoke design created by VPN networks. Thus, users can have access to the cloud applications they need without additional delay.
Has the large-scale transition to remote work increased the threat?
The risk is higher when the employees work outside the office. In the office, an employer tends to have a lot of control over them. Now organizations need to consider all the networks employees connect as hostile.
It's time to stop thinking about connecting computers to networks and start thinking about connecting users to applications. Effective authentication and authorization are excellent for secure access.
How does the transition to the cloud affect security?
As part of any digital transformation, you need to supervise the data you move to the cloud. And you should still be aware of how and where the organization provides its security. The company has to maintain the same level of data protection; wherever the worker does their duty: at or outside the office. If you don't have such rules, criminals will figure out and target where you are weakest.
What are the main threats or types of attacks currently facing organizations?
Recently, due to the massive transition of employees to a remote work format, phishing attacks tremendously increased.
There have also been many ransomware attacks. Many of them related to how people got access to their network. Before Covid, the number of people connecting via VPN could be only 10% of the organization. But now the whole company uses VPNs – and since users are very poorly versed in passwords, and we often re-use them, there is an elevated risk of using hacked credentials against your VPN to check if they work. Then, as soon as they get into the network, they will have the opportunity to encrypt your data and demand a ransom. If you don't want to pay it, they can hit you with an encryption replay attack, data disclosure, DDoS, as well as notifying your customers about the attack. All of this causes damage to the reputation.
How will security be adapted?
The future of work fits very well into the edge model of the secure access service. It's about security between users and applications; users no longer need to be present in the office; they can be anywhere, and applications can be anywhere, and the organization can still have the same level of security. The main aim is to secure the applications, leaving users and access managed by the cloud. Companies and organizations must also provide maximum technical safety while significantly increasing usability.
This article is based on an interview with an expert, Director of Security Technology and Strategy EMEA in Akamai, Richard Meeus. The original interview can be found here.
If you find our posts compelling, you can subscribe here. If you have any questions, you may write to info@digt.com: we will be delighted to get feedback.